I'm a quite happy OpenVPN user who, for security and performance reasons, decided to switch everything to Wireguard.
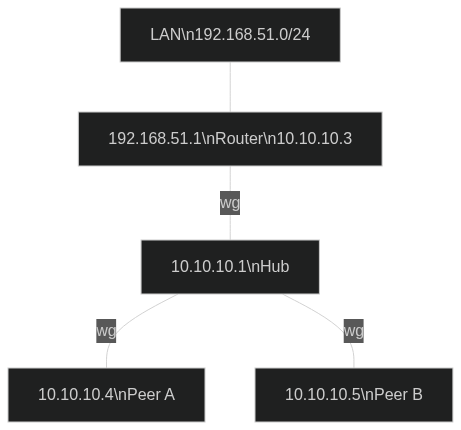
The main target is to be able to access the office private lan from outside. Both office router and outside peers are behind firewalls so I decided to adopt a Hub and Spoke configuration. The hub is on a linux cloud VPS with public IP. The configuration is the same I currently adopt with OpenVPN: there is a server accessible from the internet and several clients that can communicate with each other when connected to the VPN. One of these is a router that expose its private LAN to the other clients.
I use the office router as WG client with VPN Fusion (it's a ASUS RT-AX92U) and I'm able to see all the other computers, both in the VPN and in the private LAN.
VPN address range = 10.10.10.0/24
LAN address range = 192.168.51.0/24
router address LAN = 192.168.51.1
router address VPN = 10.10.10.3
wireguard hub = 10.10.10.1
peer A = 10.10.10.4
peer B = 10.10.10.5
The main issue is that I cannot connect directly to the router from the VPN. Both 10.10.10.3 and 192.168.51.1 are not responding. Also ping doesn't work. I don't understand if it is due to the firewall or to the WG configuration. With OpenVPN everything works fine. Of course the router is accessible from the private LAN.
I found similar questions but I already tried the suggested solutions without success. There is something I'm just not getting...
Please find here below the configuration file for the hub:
[Interface]
Address = 10.10.10.1/32
ListenPort = 51820
PrivateKey = ************
PreUp = iptables -t mangle -A PREROUTING -i wg0 -j MARK --set-mark 0x30
PreUp = iptables -t nat -A POSTROUTING ! -o wg0 -m mark --mark 0x30 -j MASQUERADE
PostDown = iptables -t mangle -D PREROUTING -i wg0 -j MARK --set-mark 0x30
PostDown = iptables -t nat -D POSTROUTING ! -o wg0 -m mark --mark 0x30 -j MASQUERADE
[Peer]
PublicKey = ************
PresharedKey = ************
AllowedIPs = 10.10.10.3/32, 192.168.51.0/24
[Peer]
PublicKey = ************
PresharedKey = ************
AllowedIPs = 10.10.10.4/32
[Peer]
PublicKey = ************
PresharedKey = ************
AllowedIPs = 10.10.10.5/32
The configuration file for the router
[Interface]
Address = 10.10.10.3/32
PrivateKey = ********
[Peer]
PublicKey = ********
PresharedKey = ********
AllowedIPs = 10.10.10.0/24
Endpoint = cloudIP:51820
and the configuration file for Peer B (Peer A is the same)
[Interface]
Address = 10.10.10.5/32
PrivateKey = ********
[Peer]
PublicKey = ********
PresharedKey = ********
AllowedIPs = 10.10.10.0/24, 192.168.51.0/24
Endpoint = cloudIP:51820
Do you have any idea? Thanks.